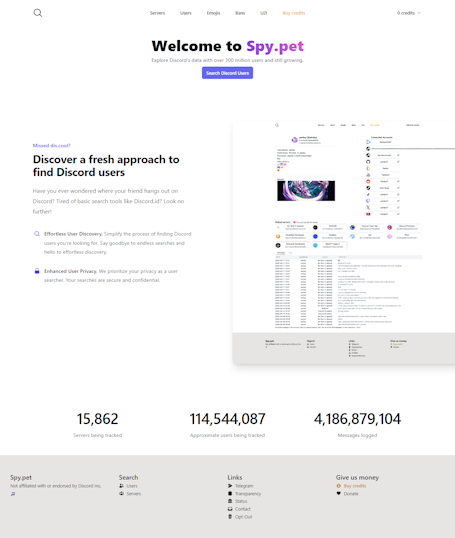
Spy.pet is a website that scrapes data from Discord, allowing anyone to pay a as low as 5 dollars to look up a user's profile, see what servers they are in, view their messages, and more. It boasts over 300 million Discord users in its database, which is still growing.
While the site claims to "prioritize your privacy" this is a blatant lie. Spy.pet is solely intended for harassment and doxing. Users can request entire Discord servers to get tracked, especially ones likely to have "interesting" conversations like politics or LGBTQ+ spaces. The owner is clearly motivated by hate, previously describing requests to track "private lgbtq Discord servers" before cleaning up that language when under scrutiny. Examples on the site were also manually edited to misgender a high profile user.
Legally, spy.pet is on incredibly shaky ground, likely violating GDPR privacy laws around consent, data storage of minors, and the "right to be forgotten". The site's new "request removal" form seems to be merely for show.
On April 19, 2024, the popular YouTuber No Text to Speech published a video entitled "Exposing the Website that Stalks You on Discord" about the spy.pet site. This launched a massive backlash against the site and its anonymous owner, later identified as going by "unknownsrc" with a history of transphobic behavior. No Text to Speech's video exposé connects the owner to the online handle "unknownsrc" through domains they control, accounts they are linked to, code repositories they contributed to, and other digital crumbs. Unknownsrc has a long history of transphobic and harassing behavior.
Its unknown if Discord is currently pursuing legal action against the individual behind spy.pet. However, with their identity and disturbing motives uncovered, it seems the site's days are numbered as as multiple groups have taken the situation into their hands to take down the site for good. What began as a way to profit off violating privacy has blown up into a wildfire of bad press that will be hard to recover from.
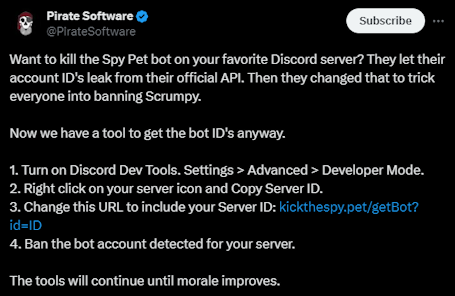
However, even before No Text to Speech published his video exposé, efforts to combat spy.pet were already secretly underway as a group calling themselves The Shadow Team was already working on a tool to help the community. On April 21st, 2 days after No Text to Speech published their video, Thor (PirateSoftware) tweeted instructions for server owners to detect and ban the bots accounts spy.pet was using.
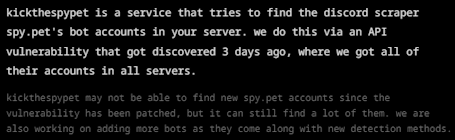
The Shadow Team had created kickthespy.pet, explaining it "tries to find the discord scraper spy.pet's bot accounts in your server...via an API vulnerability...where we got all of their accounts in all servers." However, they warned this was just a "snapshot" as spy.pet could create new bots.
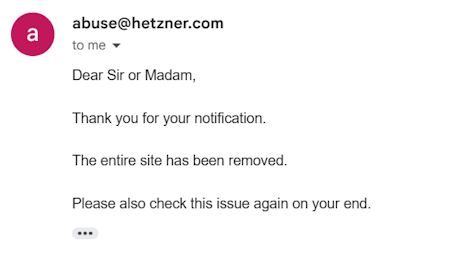
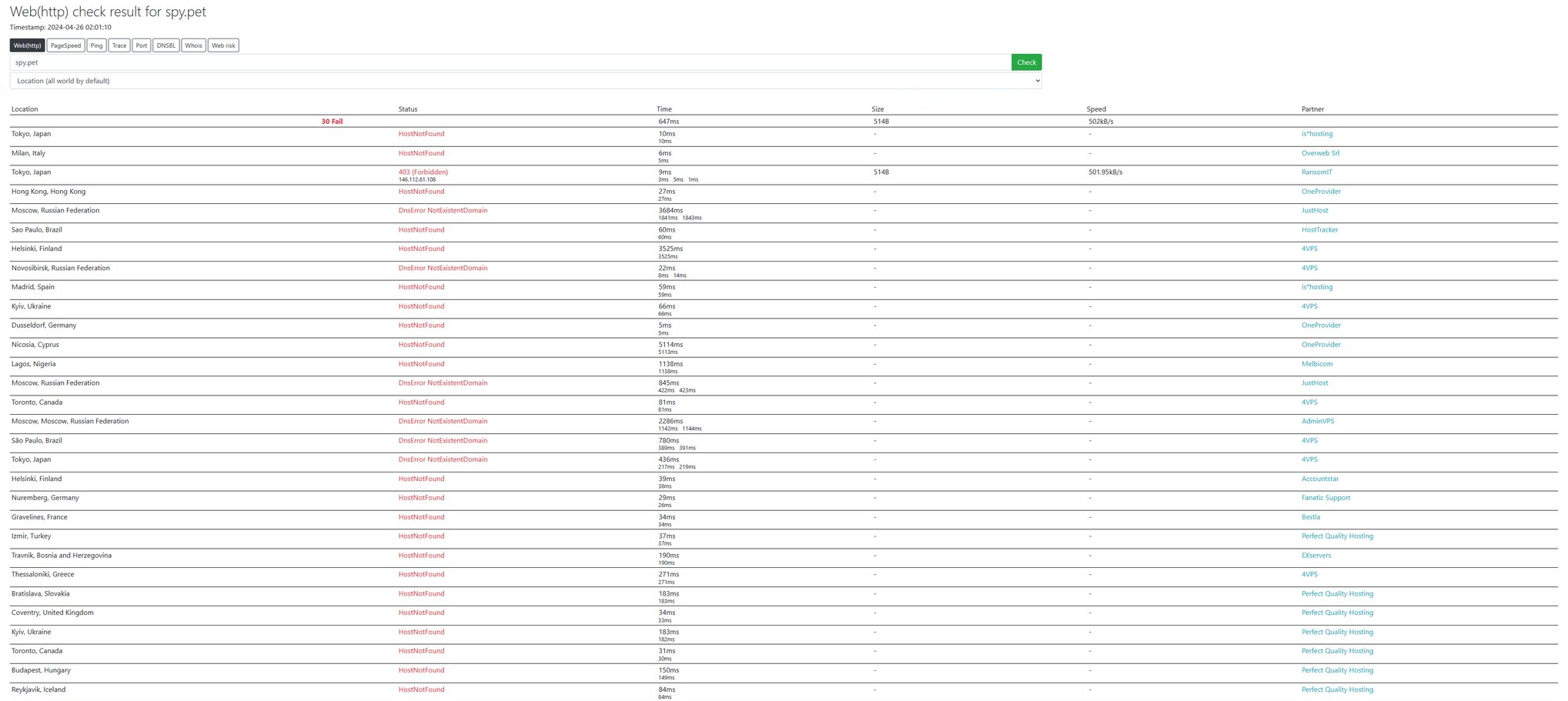
In parallel, another group called The TaskForce comprised of security researchers and developers formed between April 22-23 with the goal of taking down spy.pet completely. Over the next few days, they analyzed the Shadow Team's data, created new detection tools, and notified affected server owners. Their efforts paid off on April 25th when they discovered spy.pet was being hosted by Hetzner cloud services with its domain registered via TLD Registrar Solutions. Providing evidence of its illegal activities led both companies to suspend the domain and terminate hosting.
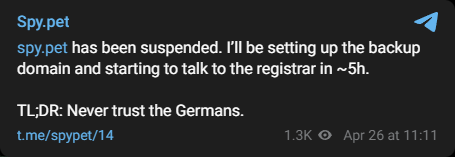
The spy.pet owner lashed out, falsely claiming on Telegram while clearly hinting at the fact that his hosting provider was indeed Hetzner: "spy.pet has been suspended. I'll be setting up the backup domain.... TL;DR: Never trust the Germans."
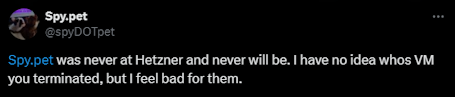
After sometime the owner of spy.pet said on Twitter: "Spy.pet was never at Hetzner and never will be. I have no idea whos VM you terminated..."
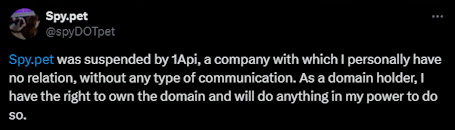
With another tweet coming later, further obfuscating: "Spy.pet was suspended by 1Api, a company with which I personally have no relation, without any type of communication. As a domain holder, I have the right to own the domain and will do anything in my power to do so."
Despite mounting evidence, the owner continued making denials and excuses in the face of their illegal operation being shut down. However, the site began going down globally as the confirmed actions took effect.
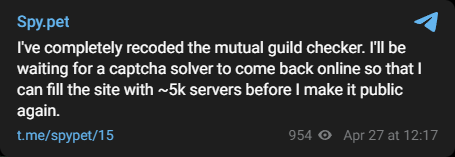
The owner's defiance continued, saying on April 27th: "I've completely recoded the mutual guild checker...I'll fill the site with ~5k servers before I make it public again."
By this point, The TaskForce had already tracked down a potential new domain called spying.pet that the owner seemed to be preparing to use. With the spy.pet domain terminated, they were closely monitoring for any resurfacing of the invasive service under a new web address. The owner's remarks made it clear this was not the end of their efforts to illegally scrape Discord users data and communications.
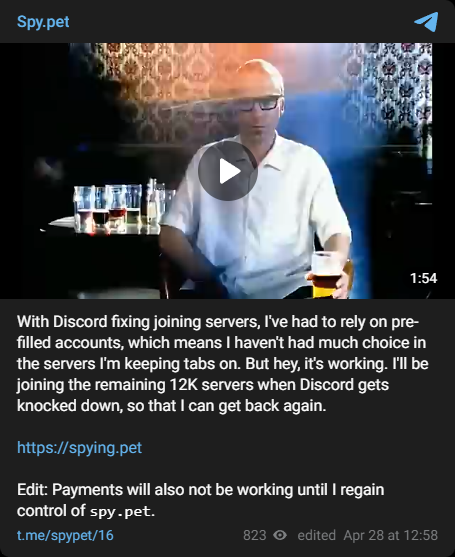
On April 28th, The owner of spy.pet had set up the site again under a new domain called spying.pet confirming The TaskForce's previous research while also stating plans to re-infiltrate servers: "With Discord fixing joining servers, I've had to rely on pre-filled accounts...I'll be joining the remaining 12K servers when Discord gets knocked down, so that I can get back again."
On April 29th, the owner of spying.pet (formerly spy.pet) posted on their Telegram channel about facing new difficulties with the spying.pet domain:
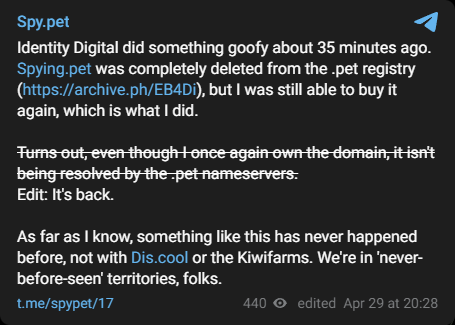
"Identity Digital did something goofy about 35 minutes ago. Spying.pet was completely deleted from the .pet registry (https://archive.ph/EB4Di), but I was still able to buy it again, which is what I did. Turns out, even though I once again own the domain, it isn't being resolved by the .pet nameservers. Edit: It's back. As far as I know, something like this has never happened before, not with Dis.cool or the Kiwifarms. We're in 'never-before-seen' territories, folks."
This came after The TaskForce had gotten in contact with Identity Digital, the .pet registry operator, and managed to delete the malicious domain from the registry. However, they failed to also suspend any reactivations of the domain, leaving the owner able to regain access by re-purchasing it.
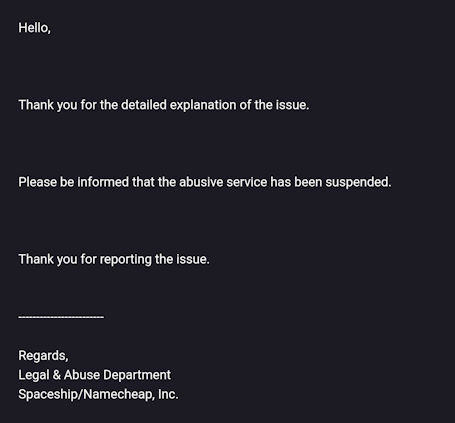
On the same day, The TaskForce continued their efforts to take down the malicious site, finally striking success on April 30th when they successfully pinpointed the hosting provider and communicated with them about the illegal activity. This led to the spying.pet domain being suspended once again, marking another victory against the invasive service.
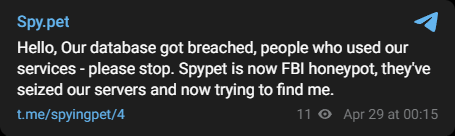
Soon after this successful takedown, the owner of spying.pet (formerly spy.pet) sent out a message on a new Telegram channel claiming: "Hello, Our database got breached, people who used our services - please stop. Spypet is now FBI honeypot, they've seized our servers and now trying to find me."
If true, this would be a major escalation, with law enforcement agencies like the FBI now directly involved in pursuing the individual behind the invasive Discord scraping operation. However, as of now, this claim comes solely from the owner's new Telegram channel, with no confirmation from trusted official sources.
It remains unclear if this message represents a legitimate legal crackdown and data breach of spying.pet's servers, or if it is merely another attempt by the owner to sow confusion and mislead people after having their illegal service repeatedly shut down. Nonetheless, it adds another layer of uncertainty to this escalating battle over privacy and harassment on Discord servers.
This escalating battle shows groups steadfastly defending user privacy on Discord against spy.pet's invasive efforts to profit off data through harassment and hate. While the site is currently down, the fight appears far from over as the owner vows to resurrect the scraping operation by any means necessary.
Both The Shadow Team and The TaskForce have made it clear they will continue monitoring for spy.pet's return, whether on a new domain or by creating new bot accounts. With No Text to Speech's video exposé also bringing widespread scrutiny, the anonymous owner of this unethical service faces an uphill battle to regain a foothold.
This article will be updated as more information gets released. Thank you for reading!